Calculating Risk Assessment Values
Your Risk Assessment Value (RAV) is calculated on the basis of 3 input variables, your
Operational Security (OpSec), your Actual Security (ActSec) and the number of Loss Controls
(LC) that you have in place, all of which have previously been defined. In order to begin, you
must first aggregate and associate all of your input information into the appropriate
categories for each input variable:
Operational Security
1. Visibilities
2. Trusts
3. Accesses
Actual Security
1. Vulnerabilities
2. Weaknesses
3. Concerns
4. Exposures
5. Anomalies
Loss Controls
1. Authentication
2. Repudiation
3. Confidentiality
4. Privacy
5. Indemnification
6. Integrity
7. Safety
8. Usability
9. Continuity
10. Alarm
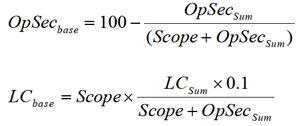
The RAV equation requires that each of the categories be assigned a base number, which
represents either the percent of the scope protected by security measures/loss controls
(OpSecbase and LCbase), or how much risk the problems cause (ActSecbase). The following
equations are used to calculate the first two base numbers, with all Sum variables as simple
sums of constituent inputs from the table above:
You should note that the sum of the Loss Control Inputs is multiplied by 0.1 – this is based on
the Loss Control category being a single input into the entire RAV equation. Therefore it must
be multiplied by 0.1 in order to normalize the 10 categories into a single input.
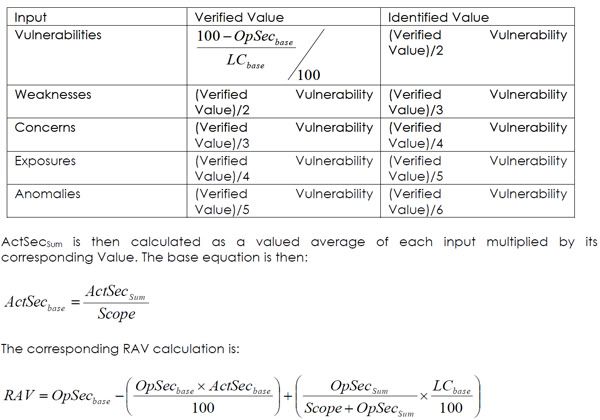
Actual Security is calculated based on values that distinguishes between an Identified
problem (identified through an interview, port or vulnerability detection scan, or assumption
based on system configuration) and a Verified problem (one that has been manually verified
by the auditor). The following value table is used to calculate the ActSecSum variable, as an
intermediate step between the Actual Security inputs and the ActSecbase variable, which is the
Actual Security basic input for the RAV equation.
There is an important distinction between the base and Sum numbers, so always make sure to
use the correct variable.
Add to My Watchlist
What is My Watchlist?