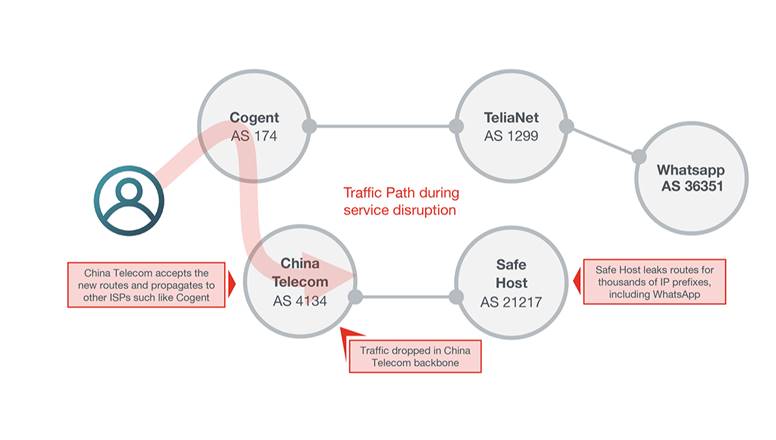
Traffic destined for some of Europe's biggest mobile providers was misdirected in a roundabout path through the Chinese-government-controlled China Telecom on Thursday, in some cases for more than two hours, an Internet-monitoring service reported. It's the latest event to stoke concerns about the security of the Internet's global routing system, known as the Border Gateway Protocol.
The incident started around 9:43am UTC on Thursday (2:43am California time). That's when AS21217, the autonomous system belonging to Switzerland-based data center colocation company Safe Host, improperly updated its routers to advertise it was the proper path to reach what eventually would become more than 70,000 Internet routes comprising an estimated 368 million IP addresses. China Telecom's AS4134, which struck a network peering arrangement with Safe Host in 2017, almost immediately echoed those routes rather than dropping them, as proper BGP filtering practices dictate. In short order, a large number of big networks that connect to China Telecom began following the route.





