The Ten Commandments of crypto security
Jun 26I feel obliged to write rules to live by in crypto, as I have seen more than a handful of people getting hacked consequently losing their precious crypto holdings.
DISCLAIMER: I am no “info-sec” expert, but paranoia can go at lengths to keep you safe from any harm it may come your way. As mentioned on previous articles, safety was one of my primary concerns before entering fully in crypto.
If you follow the Ten Commandments of crypto security, you can be certain the god of security will keep you safe from the dark forces of hackers:
1. Do NOT use SMS 2FA on your accounts
In order to open an account on any digital platform, you always need to provide an email, which is always used for password recovery, this is regular modus operandi. If your email is compromised, it is almost certain you will not recover it, and therefore any account that is linked to it could possibly be compromised as well.
In most countries is very easy to port a phone, meaning somebody that is not yourself could claim your phone number, and divert every call or SMS (text message) to a new device.
Once a hacker ports your number, if he for some reason knows your email, without knowing your password, can easily request password recovery through SMS 2FA (if its enabled), and compromise your email.
This is why you shouldn't use texts for two-factor authentication
For a long time, security experts have warned that text messages are vulnerable to hijacking - and this morning, they…www.theverge.comCoinbase vulnerability is a good reminder that SMS-based 2FA can wreak havoc
Two days ago, a friend who invested in Bitcoin asked me how secure her Coinbase investment was. She had plans to put…techcrunch.com2. Setup 2FA or U2F on your accounts
If you don't follow commandment #1, it does not matter if you have the best 2FA or U2F enabled, an enabled SMS 2FA will circumvent any security measure in place.
Two-factor authentication (2FA), keeps hackers, phishing, attempts at bay because once it is enabled on your email account, anybody that tries to break into your email would need to have physical or remote access to the device you have the 2FA app installed (either Google Authenticator or Authy) in order to produce the Time-based One-Time Passcode (TOTP) directly within the app.
An even more secure measure than Google Authenticator or Authy 2FA apps is U2F. Universal 2nd Factor, or U2F, is an authentication standard developed by the FIDO Alliance that is designed to be open, secure, private, and easy to use. The U2F device plugs into your USB port and when tapped or when the button is pressed it sends a signed response back to the U2F device to validate your login.
It's safer than regular 2FA, because its “physical key”. For example if a hacker, achieved remote access to your device where you have installed your 2FA app (Google Authenticator or Authy), he could easily get access to ALL of the authenticators accounts within the app. If a hacker wanted to get access to your account and you have U2F enabled, he would need physical access to your U2F key, reducing considerably the vulnerability vectors, as U2F cannot be remotely acquired, duh.
3. Get a hardware wallet, and USE IT!
Indisputably the safest way to store your crypto is in a hardware wallet. There is a very common saying in crypto:
“If you don't own your private keys, you don't own your crypto”.
People say this very frequently in crypto, because its very precise, if you keep your crypto in exchanges you do not own the private keys of the crypto you keep there, the exchanges do. I don't need to remind you what happens to the funds of exchanges that got hacked like Mt.Gox, Coinrail, Bithumb, Bitfinex, just to mention a few.
But aside from safekeeping your precious private keys, if, and only if stored in them (I know too many people that own hardware wallets but rarely use them), it has a unused functionality, the U2F.
For the love of god of infosec, do not store private keys on Evernote, or Dropbox, use your hardware wallets. Worst case scenario keep the private keys offline, on a paper wallet.
Hardware wallets like Ledger, and Trezor have the U2F functionality. A very cool feature that also keeps safe your private key, also protects your U2F, if it gets stolen your thief would need to know your PIN in order to use it, unlike traditional U2F (Yubico) that grants access just by plug in them in.
Ledger Wallet - Hardware wallets - Smartcard security for your bitcoins
Ledger Wallet is a smartcard based Bitcoin hardware wallet bringing maximum protection level to your bitcoins without…www.ledgerwallet.comTrezor Hardware Wallet | The original & most secure bitcoin wallet.
Discover the secure vault for your digital assets. Store bitcoins, litecoins, passwords, logins, and keys without…trezor.ioYubico | YubiKey Strong Two Factor Authentication for Business and Individual Use.
Instant, secure login to all IT-systems The #1 security key to prevent costly data breaches. Loved by users. Radically…www.yubico.com4. Don’t be a flashy douche
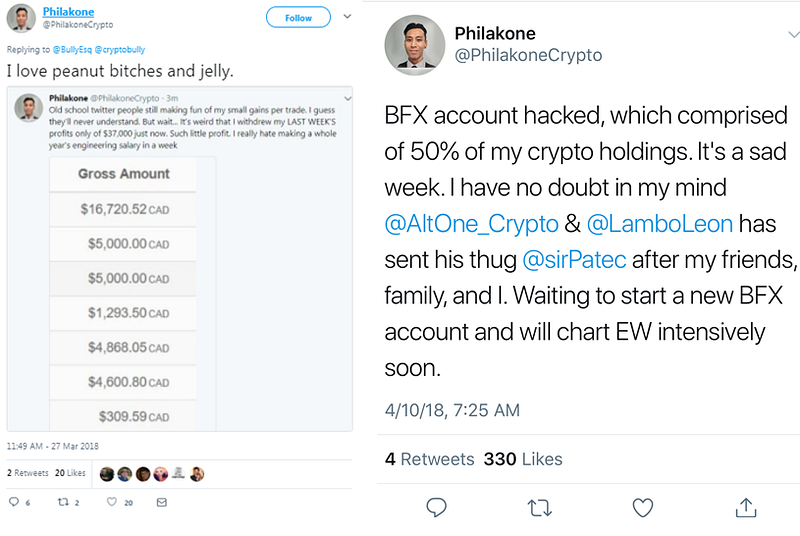
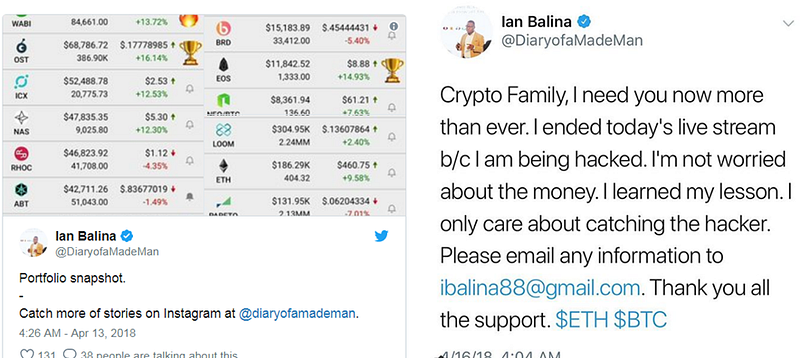
Time after time you see crypto personalities bragging about their gains in social media, and then saying they got hacked. Action, and reaction.
Exhibit A: “Don’t be a flashy douche”.Exhibit B: “Don’t be a flashy douche”.Talking openly about your gains in social media is like putting a big sign on your forehead saying:
“I AM LOADED, PLEASE HACK ME!”
If you are giving proof of your gains, you are just incentivizing hackers to try harder to find a vector of vulnerability on your infosec, and if you have any, they will find it, and exploit it, they will be rewarded handsomely. Don't be that guy.
5. Be anonymous
Being anonymous in crypto Twitter adds another layer of security between you and anybody that could try to hack you or harm you, why?
Being anonymous grants you the ability to be anybody you would like, avoiding straight up releasing to the whole world your true identity, gender, age, race, nationality, background, and so forth.
In many countries openly saying you are into crypto in social media is like putting out a commercial ad that you are loaded, in extreme cases it could bring harm your way or to friends or family members, through theft, kidnapping, or extortion.
You could be a anonymous flashy douchebag, and could get away with it, cause you make yourself a way harder target to creep on.
Will online anonymity win the war of openness vs privacy? - Jamie Bartlett | Aeon Essays
Let's see if this rings any bells. Back in the early 1990s, just as networked computing was taking off and millions of…aeon.co6. Don’t dox yourself
If you are either anonymous or non-anon, avoid doxing yourself, dont share your personal information on social media, either written or by pictures.
A very common way of doxing yourself is by sharing pictures of the surroundings of where you live. Little by little you provide pieces of the puzzle to someone to figure out more about you.
Every lead you give away of your personal information, can be used by hackers to fill out the puzzle on finding a vector of vulnerability to get access to your valued crypto assets. Do not be an easy target for social engineering.
Social Engineering Attack | Cloudflare
What is social engineering? Broadly speaking, social engineering is the practice of manipulating people into giving up…www.cloudflare.com7. Different email for different types of accounts
Avoid using the same email in your social media and your exchanges accounts. Social Media accounts are easier to hack than crypto exchanges, as an example:
- Twitter does not have non-2FA, and as default does not request you to login every time. Possibly someone could acquire your email if you don't lock your work computer or log-out.
- It is widely known that Facebook shares and sales private user information with third parties, probably your email and many other delicate information.
This said, compartmentalizing the emails you use according to the level of importance could help mitigate your exposure to hackers.
As an example, use one email for Twitter, Facebook, Instagram, Snapchat, Dropbox, Evernote, etc; and another email only you know for your exchanges. If any of these non-exchange accounts get compromised, or their companies decided to sell your email and data which is very likely to happen, at least that email is only linked to those accounts and not to your exchange-bank-like account.
Or even more secure, use different emails for each exchange, emails that you solely use for those specific exchanges. The challenge here would be email and password management for these accounts, but paranoia can do wonders.
Needless to say, avoid using same passwords throughout your accounts, if so you are facilitating your hackers work.
7 Reasons to Have More Than One Email Address in 2018 - Mailbird
Why have multiple email addresses you might ask? When setting up an email account, your first instinct might be to…www.getmailbird.com8. Bookmark websites
The easiest way to lose crypto by far is through phishing websites. Picture you just acquired a new laptop, your mobile rings because you have John Mcafee mobile notifications on, you quickly open Internet Explorer to login to Binance to do a quick fomo trade. You go to Google, type Binance, an inadvertently click on the first phishing Binance search result, you type in your email and password, (lets think you are lazy enough to no have yet enabled 2FA).
Boom, you just lost all of your funds in Binance, and possibly all your funds in every other crypto exchange. Its cheap to create identical websites to the real deal, pay Google Ads to have them on the top, and also very profitable.
This happened also to MEW few times, so thread carefully, avoid accessing links of exchanges on Google, preferably type it in on the address bar or even better access them through your saved bookmarks.
Scammers are tricking people to log into fake cryptocurrency exchange sites, and they're incredibly…
Reddit user "chrysotileman" posted a screenshot of a fake cryptocurrency exchange site "coinsmarkets.com." If you're…www.*.com9. Use VPN on untrusted WiFi
Using WiFi of unknown trustworthiness, is like having sex without a condom with a complete stranger. Using a VPN on public WiFi networks helps you avoid getting cyber venereal diseases like WiFi spoofing, Honeypot attack, or Firesheep.
VPNs: What They Do, How They Work, and Why You're Dumb for Not Using One
For as ubiquitous as connectivity has become and how reliant we've grown on it, the Internet is still a digital…gizmodo.comHow a VPN Can Boost Your Security and Privacy
Ask any security professional about strengthening your computer's security, and he or she will advise setting up a VPN…www.tomsguide.com10. Antivirus and Firewall yourself
Antivirus protects your computer from within, from malware. So if you installed a wallet from a “proof of stake/master node” coin someone shilled you into buying, you better be sure to have a good antivirus to avoid having malware on your computer.
Firewall protects you from unwanted incoming connections to your computer, aka people trying to gain control of your computer (hackers) from the outside.
People grow increasingly confident about how much information they disclose about themselves on the internet and specifically on social media, thinking they are “safe” because they are behind a screen that protects them from real world dangers.
Think again, you are as susceptible to dangers as if you were walking in real world streets, the difference is that you are sharing your thoughts, your pictures, your persona, your real world personal data with millions of people instead of a few thousands.
Behave in this digital age as you would in the real world, be cautious, don't be flashy, practice safe digital behaviour as you would in real life. Use common sense, there is more people and malicious software, AI watching you than you think.
If you enjoy the read, follow me on Twitter, is good for Karma.
Panama Crypto
₿itcoin, tech innovation, drones. Industrial engineer by education, marketing degenerate by profession. twitter.com/Panama_TJ
- Forums
- CFDs
- Crypto security